According to F-Secure’s latest Mobile Threat Report, the number of mobile malware threat families increased by more than 25% in the third quarter of 2013, the latest data available, and this rapid increase shows no sign of abating. The threats overwhelmingly target Google’s Android operating system, with very little malware on iOS, Blackberry, or Windows phones. Using Recorded Future, one of Praescient’s partners, we can quickly see the increase in mobile malware just over the past several years.
Mobile malware has been around for 10 years—in early 2004, Cabir, probably the world’s first mobile malware, infected Nokia phones via Bluetooth. Bluetooth malware is clunky and obvious—it can only be spread to other phones in the immediate vicinity, and a user has to accept the file over Bluetooth and agree to install it—all this assuming that the user has Bluetooth turned on and in discoverable mode.
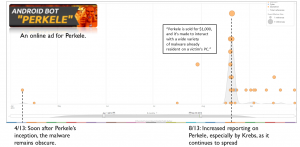
But mobile malware has come a long way since the early days. Last year, mobile malware called “Perkele” affected users in a wide swathe of the world from Europe to Asia who use text messages (which contain mTANs) to confirm bank transactions. Those affected included customers of large, multinational banks like HSBC, ING, and Citibank. The malware prompted users to download a phony “security application” to the phone in order to complete the sign on process. Once the user complies, text messages can then be intercepted on the phone.
By intercepting these text messages, malicious actors can work around security measures and initiate a financial transfers from the victim’s bank account. Masking the transfer on the user’s computer, this technique can make it look like the transaction never took place when the user is looking at his or her balance and recent transactions. It could be days or weeks before the unwitting victim realizes the funds have been transferred, perhaps swiping his or her debit card at a store and scratching their head when the transaction is declined.
In fact, Perkele isn’t considered to be particularly sophisticated in the world of mobile malware, where some malicious apps are capable of enabling an Android phone’s Wi-Fi and sending data to a remote location—or even hopping onto someone’s PC to turn on the microphone. A security researcher in January announced a proof-of-concept of a particular type of mobile malware could be used to crack a user’s passwords as financial service and other apps.
Constant monitoring, whether related to mobile security or cyber security more generally, allows an organization to focus on averting threats. Smart analysts and advanced analytics let an organization focus on the most relevant cyber security threats.